
How to crack password from hashes with a hash suite
To comprehend how to crack password hashes effectively, it’s essential to grasp the fundamentals of password storage, the nature of hashes, and their various types. Without a clear understanding of these concepts, utilizing the hash suite tool for password cracking becomes challenging.
Table of contents
- So what is password hashing?
- Commonly asked questions about hash suite
So what is password hashing?
Storing usernames and passwords in plain text on devices and servers poses an immediate risk of compromising all stored passwords. If the password file is breached, these passwords become vulnerable to easy exploitation through cracking methods.
Within operating systems like Windows and Linux, various cryptographic hash functions, re employed to convert stored passwords into complex, unreadable hashes. These hashes are one-way transformations, making it impossible to reverse-engineer a password from its hash alone. The hash suite operates on a trial-and-error basis, generating and comparing different candidate passwords and their corresponding hashes against the stored data.
Rather than “inverting” the hashes to retrieve passwords, the hash suite systematically generates and matches hashed passwords. For further insights into password cracking methods, additional information is available here.
You might like: Hacking facebook passwords with facebook password extractor.
Download hash suite
The hash suite can be downloaded from here.
Extract the zip file and open the one corresponding to your device version. Mine is 64bit.

The welcome dialogue box will be shown. Click on ok or enter to dismiss it.
Now you have to download the necessary world lists. You can do this, as shown below.
The downloader option has wordlists for downloading.
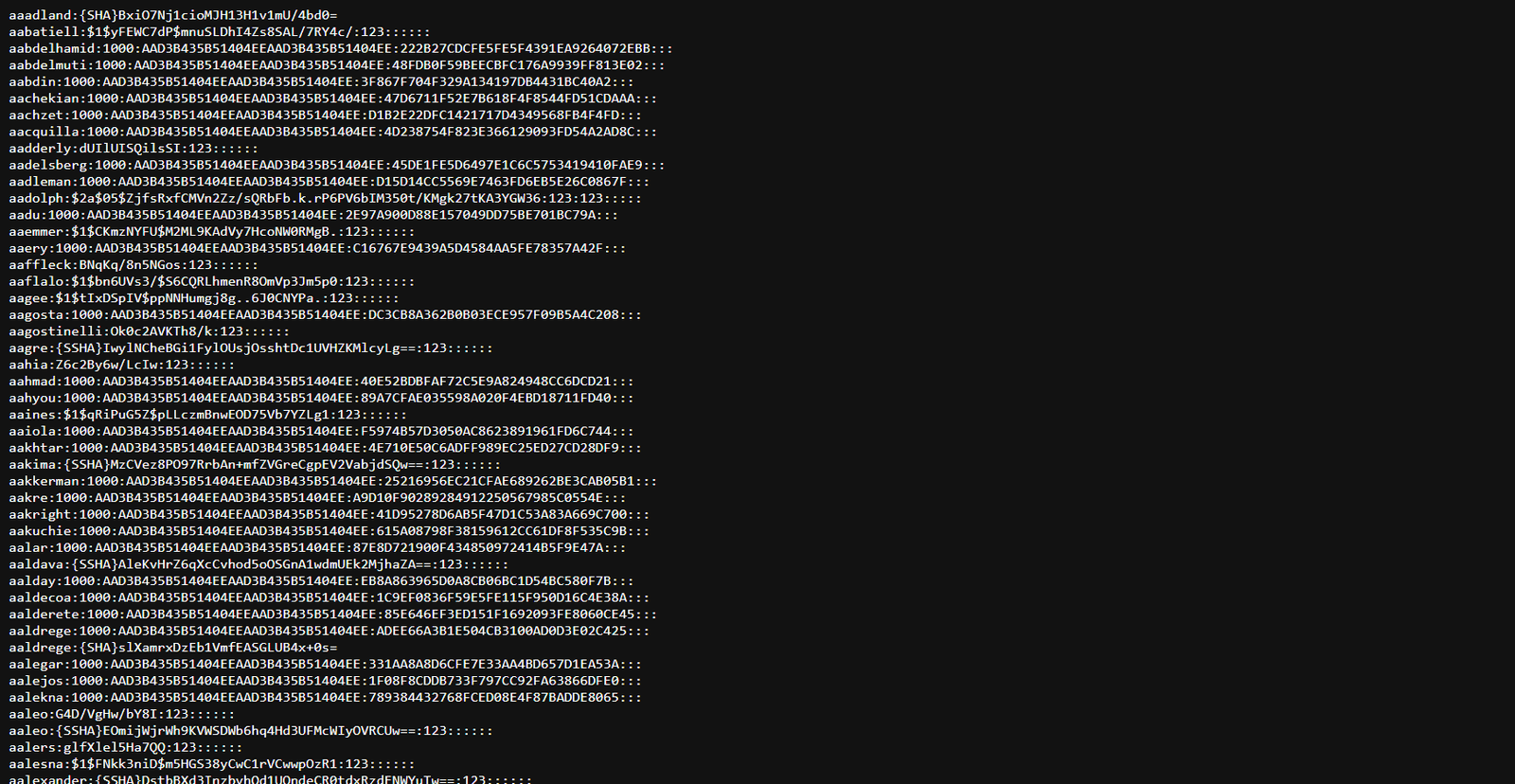
Step 1: Obtain the password hashes
To crack password hashes, we first need to get them. Normally you obtain these password hashes after exploiting a machine with a remote exploit. More articles regarding the same will be added soon; however, we will be using hashes from the public demo (available from here). These are publicly available hashes of common passwords. You can use them for testing.
Step 2: Cracking LM hashes
LM hashes are very weak: we can crack ANY valid LM hash password by brute-force (Learn more about LM hashes here).
We start with nothing cracked yet:
| 00h:00min | LM: Found 0/3380 0% | NTLM: Found 0/30640 0% |
The hash suite defaults to using the Charset key-provider and a password length range from 0 to 6, which it automatically selects.
Now we will start the attack by clicking the start button.
| 00h:02min | LM: Found 1663/3380 49% | NTLM: Found 0/30640 0% |
An hour later, we cracked all the passwords, as depicted below.
| 00h:29min | LM: Found 3380/3380 100% | NTLM: Found 0/30640 0% |
Step 3: Crack passwords with word lists
Use Wordlist with the file Wikipedia-wordlist-sraveau-20090325.txt.bz2.
I recommended downloading these lists at the beginning of the article. We are going to use this list to crack some passwords.
| 00h:31min | LM: Found 3380/3380 100% | NTLM: Found 6900/30640 22% |
We will use the Charset key-provider with default options, which are: password length from 0 to 6 with all printable characters.
| 00h:33min | LM: Found 3380/3380 100% | NTLM: Found 7707/30640 25% |
Step 4: Crack passwords by using common English phrases
The popularity of passwords based on English phrases has risen quite a lot lately. Hash Suite provides a phrase generator with English words that can also be used to crack passwords.
This obviously takes a long time to process and the entire hack to finish. Have patience. The cracking process will depend on your device’s speed. Do make sure your device is properly cooled, especially if you are using a laptop.
Step 5: Try all other methods for hacking passwords
With each update, additional methods such as charset, phrases, wordlist, DB info, keyboard, LM2NT, among others, are incorporated for password cracking. Each method—whether it involves NTLM, MD5, SHA1, SHA256, SHA512, DCC, SSHA, MD5CRYPT, DCC2, WPA-PSK, or crypt hashes—is functional. Exploring the tool’s numerous features would be beneficial. While I can’t cover all its aspects, I suggest installing and testing it to gain a comprehensive understanding.
Hash Suite Key-Features for cracking passwords
Hash Suite offers many different ways (named key-providers) to generate passwords:
Charset generates passwords through exhaustive combinations, also recognized as a brute-force attack. Wordlist, on the other hand, generates passwords based on predefined wordlists. Keyboard operates by attempting combinations of neighboring keys on a keyboard, while Phrases create password phrases by merging words from a specified wordlist. Additionally, DB Info generates keys using all usernames or found passwords, particularly advantageous when paired with enabled rules. Lastly, LM2NT adjusts the character case in cracked LM hash passwords, facilitating the instantaneous cracking of corresponding NTLM hash passwords.
Review all the cracked passwords.
The hash suite enables straightforward review of all broken passwords. With a robust device and the patience for the cracking process to conclude, many passwords can be cracked using this suite. However, it’s crucial to note that very strong passwords remain impervious to hacking through this tool. This fact underscores the importance of always creating a robust, difficult-to-crack password.
Commonly asked questions about hash suite
Q1. Can you crack any password with this tool?
Technically, yes you can provide the password you want to crack available in a password list, and you have the hashes locally available on your system for hacking. Your device performance will also come into the picture.
Q2. What is the purpose of the HASH suite?
This tool serves the purpose of scrutinizing passwords to guarantee they adhere to the minimum security standards. Furthermore, it enables companies to conduct audits on employee and network passwords, ensuring compliance with the established requirements.
Q.3 Can I use this to hack WhatsApp and facebook?
You absolutely cannot hack WhatsApp or any other messaging service like WhatsApp.
Q.4 Is this tool legal to use on anyone?
While not intended for hacking, this is a pentesting tool crafted by developers with noble intentions, akin to the creators of the renowned password cracking tool, John the Ripper
I hope you liked the article do share the article. You can show your support by donating to the website.



