
10 Best Internet Search Engine Used by Hackers
We all use the Internet search engine in our daily life whether to search for a recipe or to complete an assignment or some other task, but have you ever wondered what kind of tools and Internet search engines hackers might be using to find out the vulnerabilities of various systems through the Internet. The hacker Internet search engine is slightly different from our normal Internet search engine because it can provide access to each and everything available on the Internet including Deep Web resources like Shodan, Hunter Search Engine.
There are a large number of search engines that hackers use for various purposes and here we have brought the best 10 out of all the hacker search engines available –
Table of contents
1. Shodan:
Hackers worldwide use one of the best Internet search engines to gather information about any Internet-connected device, including webcams, alarms, servers, routers, traffic lights, and various others. It provides extensive details in the form of IP addresses, HTTP server banners, device locations, and device types, which they can employ to uncover security vulnerabilities and either rectify them or exploit them for breaching the system’s security.
Also, Read- An In-Depth Article on What is Shodan and How to Use it
2. Censys:

Censys, similar to Shodan, monitors connected and exposed devices on the internet, gathering data and presenting it through a search engine. Users can access reports and data on the deployment and configuration of websites, devices, and certificates. Additionally, Censys enables real-time access to information about attacks on computer systems by discovering vulnerable services and unpatched routers.
3. Greynoise:

Unlike Shodan and Censys, Greynoise allows you to identify servers and users that are scanning various networks and devices for vulnerabilities using search engines like Shodan or even more advanced and malicious ones. Using Greynoise we can get information about malicious websites, types of attacks, and breaches in systems by typing the IP address or some related keywords. It is very useful for hackers and security personnel that deal with thousands of IP addresses to filter out unwanted internet background noise that interferes with hacking or security operations.
4. WiGLE:
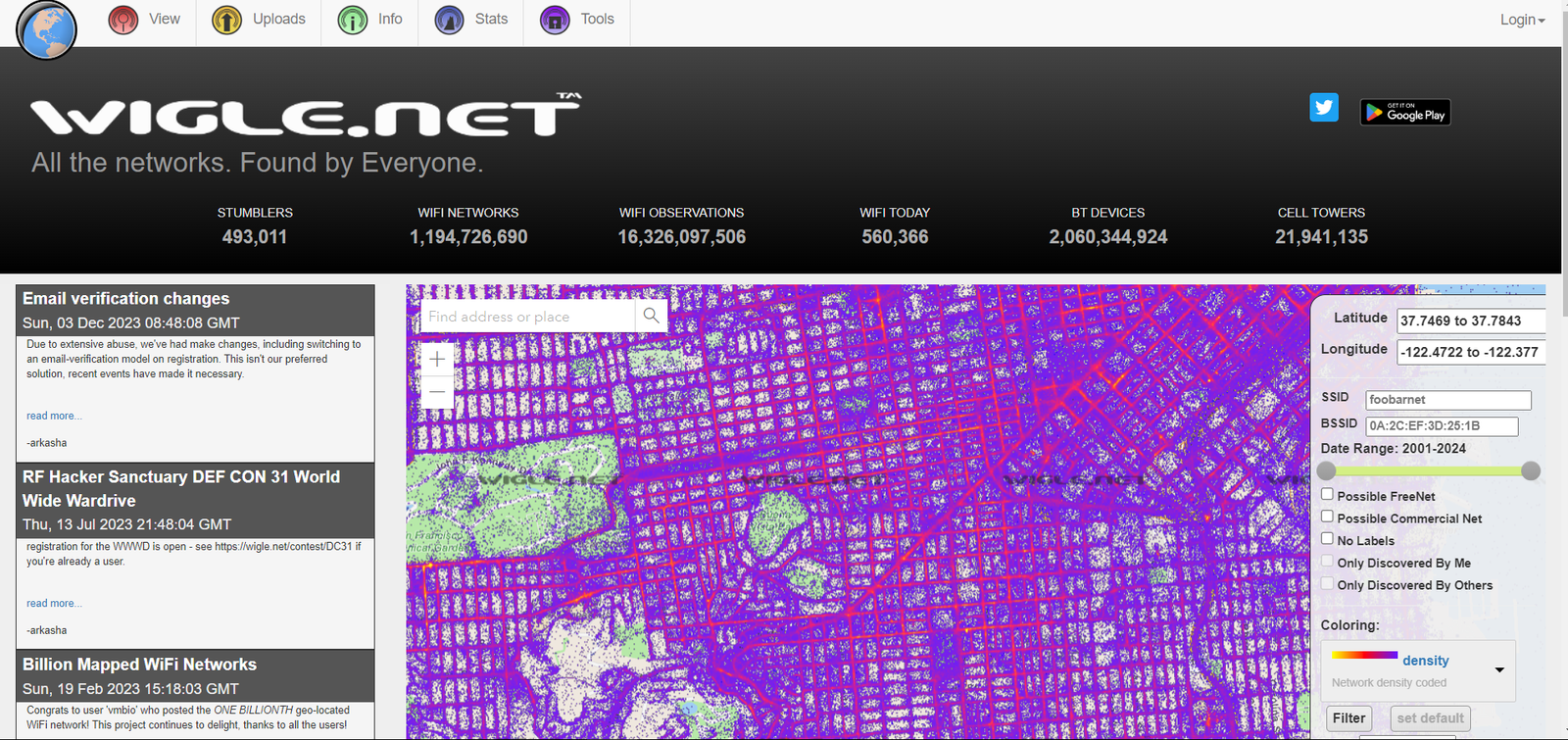
Wigle is an Internet search engine to find wireless networks through coordination and is used for wireless network mapping. It shows a map where we can enter latitude and longitude to find all the available hotspot networks, Wi-Fi devices, and telecommunication antennae’s in that particular area. It can be used to identify and monitor insecure systems that are vulnerable to attacks or just for finding open networks in a particular area.
5. Zoomeye:

Developers created this hacker-friendly tool primarily for the Chinese market, enabling users to navigate and discover vulnerabilities and threats within networks and systems. It gathers extensive data from various sources such as websites, devices, and administrations. Users can access this data by inputting queries, IP addresses, device names, or related keywords. Additionally, it provides statistics on exposed devices across different countries, browsers, servers, and more.
6. Hunter:
It is the most used and dynamic Internet search engine used by hackers for email address detection. Hunter Search
Engine can be used to find and retrieve all the email addresses that are associated with a certain domain
or organization. All you have to do is enter the name of the company in Hunter and the search.
The displays a list of verified email addresses that come under that domain including their activity,
and the public resources that were used r those addresses. The developers have also created an API to check whether an email id is deliverable and get additional information on the organization.
7. PIPL:
PiPl is a useful Internet search engine for finding information about individual persons using the
phone number and email address and identifying them. It is the largest people search engine in the world. It can reveal everything about a person, including their name, contact, personal information, professional information, etc.
8. PublicWWW:
The search engine allows users to find source code, such as HTML, CSS, and JavaScript, present on any webpage. By entering a snippet of code into the search box, the engine generates a list of websites and webpages that have utilized similar code, enabling users to search for alphanumeric extracts, signatures, and keywords within specific webpages.
Also, Read- 30 Websites to Get Personal Information of Anyone
9. HIBP:
The “Have I Been Pwned” internet search engine identifies whether a specific email account has been compromised due to a data breach, exposing the information and potentially being used in some way. It gathers and analyzes various database dumps to identify disclosed accounts. If the tool detects a compromise in a particular account, it provides detailed information about the breach and the type of information involved. If the account has no associated data breaches, it displays in green color stating, “Good news – No pwnage found.”
10. OSINT Framework:

The OSINT Framework, an acronym for Open Source Intelligence Framework, collects information available from public sources for assessment purposes. Upon opening the framework, users encounter a list of various categories, each containing its own submenus. They can navigate through these options to access desired results, which open in a new tab through the search engine. This framework plays an essential role in cybersecurity and finds extensive use in law enforcement, national security, and other intelligence services.
The above-mentioned search engines can prove to be quite useful if you are doing penetration testing or
checking for security breaches to rectify them. Some of them such as HIBP are useful for common people also.
Hackers all over the world actively use these search engines to find faults in systems or gain information
about potential targets.
Also, Read- How to Hack Windows with text and Zip File



