
7 Password Cracking Attacks that Still Work in 2021
With the increase in Internet users all around the world, the number of cybercrimes is also increasing at a very rapid rate. The first thing that comes to mind when we hear security is “password”.
Nowadays everything that is available on the Internet requires you to create an account that definitely consists of a password.
In present times, most people don’t pay much attention to their security and passwords that result in a large number of cybercrimes and the rise of password cracking tools like a dictionary attack, brute force attack, mask attack, password guessing attack, and more.
Having knowledge about the various password cracking techniques is essential not only as an ethical hacker but also as a common person because it can help you prevent such an attack.
A hacker performs some of the most commonly used password cracking attacks.
Table of contents
Dictionary attack:
A dictionary attack is slightly more sophisticated than a brute force attack. In this type of attack, the attacker loads a dictionary file into the target system that runs against user accounts.
This attack gets its name from the same fact that the attacker methodically tries to enter every word in
the dictionary in order to crack the password.
This also removes the randomness of a brute-force attack to some extent thereby
reducing the amount of time needed to find the password—provided that the password is present in the dictionary.
The reason for the success of this attack is user negligence towards creating a strong password
which benefits the hacker by making it easier to crack the password using lesser combinations.
In order to prevent ourselves from a dictionary attack, all we can do is make our passwords complex by using a combination of different and random dictionary words as well as numbers and characters for higher complexity and better security of the password.

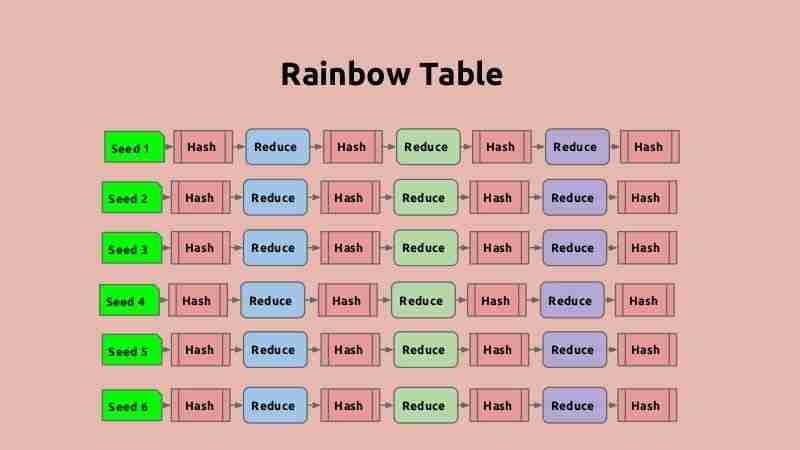
Rainbow Table attack:
A rainbow table attack is a special type of dictionary attack since it uses specially optimized dictionaries for cracking purposes that contain common hash values as well as passwords.
The server stores all the passwords as a hash string to prevent any kind of password misuse.
Hackers attempt to access these hashes by using a rainbow table, which is a list of pre-evaluated hashes of all possible password combinations. Cracking a hash code enables easy retrieval of the password from it.
To prevent this attack, we use a technique called the Salt Technique, which involves adding some random data to the password before hashing it.
Brute-force attack:
A brute-force attack is a password cracking attack based on password combinations. The attacker in this attack aims to crack the password by submitting different combinations until finding the correct one.
However, most attackers automate the process by using software that runs exhaustive password combinations in a significantly lesser time span.
It is a really powerful attack for cracking smaller passwords but when it comes to longer passwords, it seems to be relatively inefficient than other attacks since a lot of time is wasted in making unlikely guesses.
This is the reason that most types of encryption techniques can effectively prevent a brute-force attack by using hashing algorithms to slow down password entry.

Hybrid attack:
A Hybrid attack is used when the attackers have an idea of the password format i.e. the password
has some sequence that can be easily recognized, for example, a software password might have
the word “software” appended with a number of other characters.
This type of attack is considered very dangerous and effective because it combines
dictionary and brute-force attacks, incorporating the abilities of both these attacks.
The attackers strengthen the dictionary attack part in a hybrid attack by placing a string of brute-force characters at the beginning or end of the dictionary entries.

Mask attack:
The attacker uses a mask attack when they have already gained some information regarding the password,
such as knowing that the password begins with a number or contains a specific special character or alphabet. They also have knowledge about the password length and the use of a certain alphabet a certain number of times. This information is useful for the attacker to narrow down the permutations and can be justified as criteria that are useful in configuring a mask.
Unlike dictionary attacks where the attacker uses lists of all the possible password combinations,
a Mask attack is far more specific in nature.
The main aim of the hacker in these attacks is to reduce the time taken for cracking a password and
also eliminate any extra processing during the procedure of password cracking. The mask attack is one of the most used attacks of all time.
Malware attack:
Malware attacks use malicious software and tools such as Keyloggers, screen scrapers, Spywares, etc.
that are designed to steal personal data.
The attacker installs the tools on the target device and they run in the background to collect the victim’s activity through keystrokes or screenshots or other methods, which the attacker then shares.
Some advanced malware even searches through a target’s system for password dictionaries or data associated with web browsers. After collecting the data from the target device, a hacker can easily analyze it to retrieve the desired system password.

Password Guessing attack:
If all other password cracking attacks somehow fail, a hacker can always try and guess your password because
it is based on the predictability of the user.
Despite the availability of tools that provide an unbreakable combination of strings, most users find it time-consuming and choose a password that they can easily remember.
These passwords are often based on things of emotional attachment such as pets or family and
an experienced hacker can easily guess this type of password by doing little research about the target.
A password guessing attack is the most dangerous kind of password cracking attack because the attacker
can crack a password without resorting to a dictionary or brute force attacks and
thus exploit the user’s data without even being noticed.

Hackers and criminals are always looking for new opportunities to crack your passwords and break in, making it very crucial to protect each and every account with a unique and strong password. Being well educated about the various types of attacks that you could be prone to is also important.
I hope you loved our article. Don’t forget to support our website. Happy Hacking.



