
Endpoint Detection and Response to Combat Threats
In today’s interconnected digital world, businesses grapple with an ever-shifting threat landscape. Malicious actors are constantly devising novel and cunning attack methods, making it increasingly challenging for organizations to safeguard their data and systems. This necessitates robust security measures, and one pivotal solution at the forefront is Endpoint Detection and Response (EDR). EDR serves as a crucial shield against these evolving threats by actively monitoring and swiftly responding to potential dangers lurking within endpoints.
What is EDR?
EDR, a crucial cybersecurity solution, offers continuous monitoring and defense against various threats that target endpoints. These threats encompass a wide spectrum, ranging from harmful software and ransomware to deceptive phishing attempts and advanced zero-day exploits. EDR or Endpoint Detection and Response, analyzes data collected from different endpoint devices such as desktops, laptops, servers, and mobile devices, swiftly identifying and responding to any unusual or suspicious activities.
How EDR Works
EDR, a cybersecurity tool, maintains ongoing surveillance of endpoints like desktops, laptops, servers, and mobile devices. Its primary function is to swiftly identify and respond to potential threats. By offering instantaneous insight into endpoint activities, it empowers organizations to swiftly recognize suspicious behavior and take prompt measures to safeguard their systems.
EDR’s Core Functions
At its core, EDR performs three crucial functions:
- Data Collection: EDR agents continuously collect data from endpoints, gathering information about file activity, network connections, process creation, and other relevant events. This data forms the foundation for EDR’s detection and response capabilities.
- Threat Detection: EDR employs advanced techniques, including machine learning, behavioral analysis, and threat intelligence, to analyze the collected data and identify patterns that indicate potential threats. This includes detecting known malware, ransomware, phishing attempts, and zero-day exploits.
- Automated Response: When a threat is detected, EDR can take automated actions to contain and mitigate the attack. These actions may include isolating the infected endpoint, quarantining the malicious files, or even removing the threat altogether.
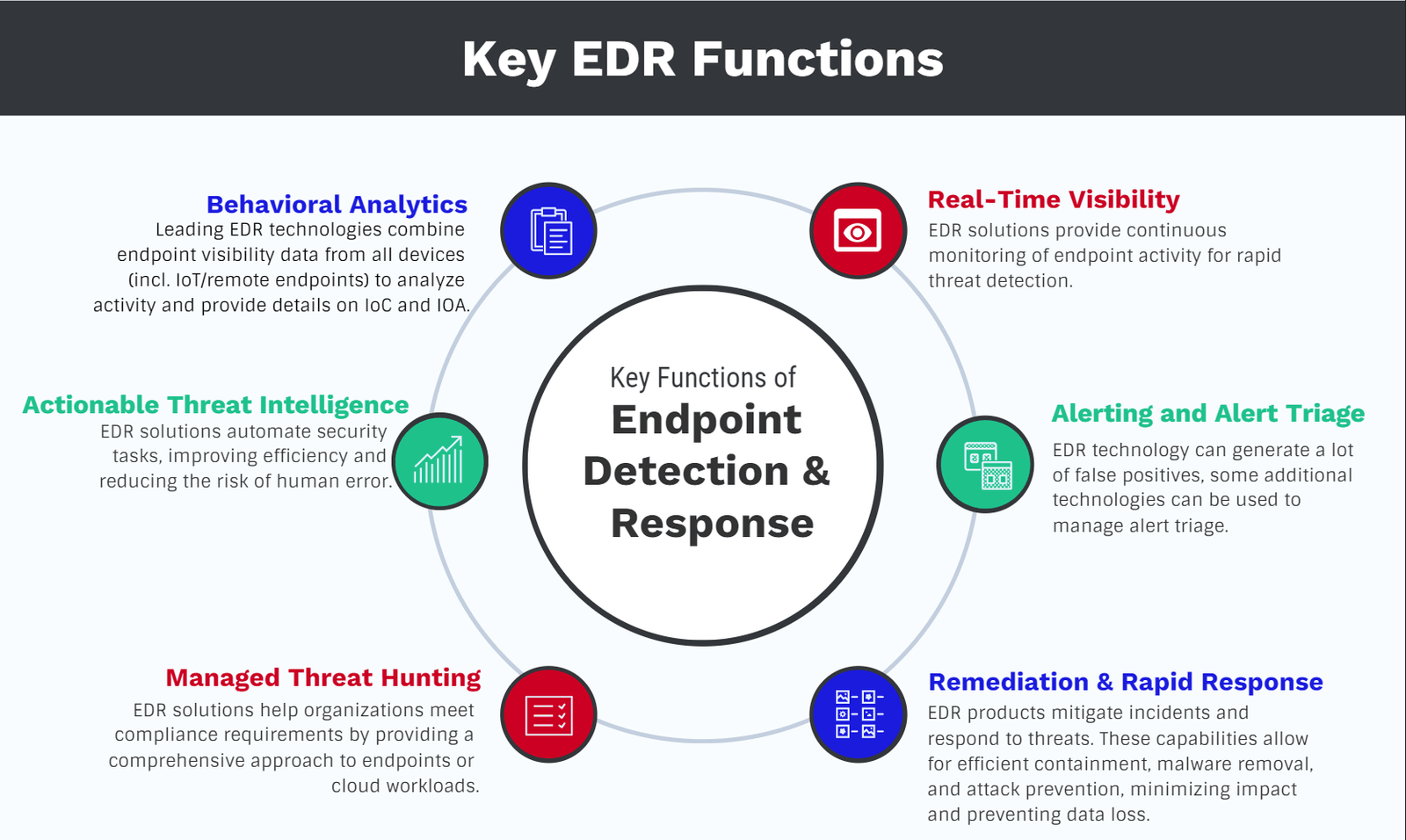
EDR’s Detection Mechanisms
EDR utilizes various mechanisms to identify and classify potential threats:
- Signature-based detection: This traditional method compares file signatures to a database of known malware signatures. If a file matches a known signature, it is flagged as malicious.
- Heuristic analysis: This method examines file behavior and characteristics to identify suspicious patterns that may indicate malware, even if the file itself is unknown.
- Behavioral analysis: Through behavioral analysis, EDR actively monitors running processes and applications, swiftly detecting anomalies that might signal malicious activities. This method is instrumental in proactively identifying potential threats.
- Machine learning: Utilizing machine learning algorithms, EDR efficiently analyzes extensive datasets, swiftly identifying intricate patterns indicative of potential threats. This approach significantly enhances threat detection capabilities.
- Threat intelligence: By integrating with threat intelligence feeds, EDR ensures it remains current with the latest threat landscapes, vulnerabilities, and evolving attack techniques. This integration equips the system to proactively anticipate and counter emerging threats.
EDR’s Response Capabilities
Upon detecting a threat, EDR can initiate various automated response actions:
- Alerting: EDR generates alerts to notify security personnel of the detected threat, providing them with essential details about the incident.
- Isolating the endpoint: EDR can isolate the infected endpoint to prevent the threat from spreading to other devices on the network.
- Quarantining the threat: EDR can quarantine the malicious files or processes, preventing them from executing further actions.
- Removing the threat: EDR can eliminate the threat from the system, restoring the endpoint to a safe state.
- Automated remediation: EDR can perform automated remediation tasks, such as patching vulnerabilities or restoring backups, to address the underlying causes of the threat.
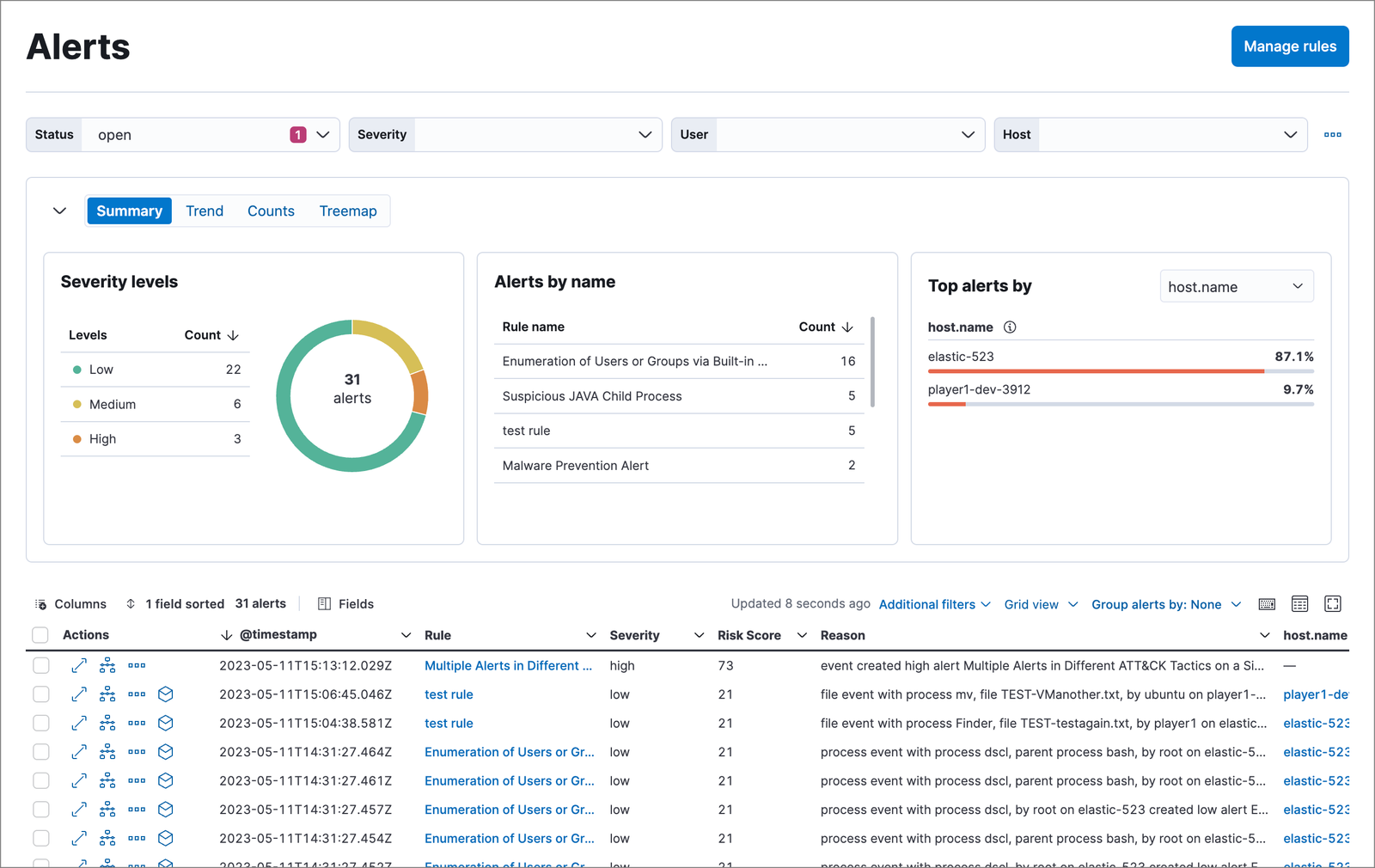
Benefits of EDR
EDR solutions offer a number of benefits to organizations, including:
- Improved visibility: EDR solutions provide organizations with a comprehensive view of the activity on their endpoints. This can help organizations to identify and respond to threats more quickly.
- Enhanced threat detection: EDR solutions use advanced techniques to detect threats, including machine learning and behavioral analysis. This can help organizations to detect threats that would otherwise be missed by traditional security solutions.
- Automated response: EDR solutions can automate many of the tasks involved in responding to threats. This can help organizations to save time and resources.
- Reduced downtime: By helping organizations to detect and respond to threats quickly, EDR solutions can help to reduce downtime and minimize the impact of attacks.
How to Implement EDR
There are a number of factors to consider when implementing EDR, including:
- Organizational Scale and Complexity: EDR solutions must harmonize with the organization’s size and intricate security demands.
- Budget Considerations: EDR solutions come with diverse pricing structures and capabilities. It’s crucial for organizations to seek a solution that not only aligns with their financial constraints but also fulfills their operational needs.
- Tailored Security Needs: Organizations must assess how well an EDR solution caters to their unique security concerns. It’s essential to ensure that the chosen solution addresses specific security requirements effectively.
Once the organization has selected an EDR solution, it is important to deploy the solution correctly and to train security personnel on how to use it.
Best EDR tools
Here are some of the best EDR tools on the market:
- Palo Alto Networks Cortex XDR: Palo Alto Networks Cortex XDR offers a comprehensive EDR solution, delivering not just endpoint visibility but also robust threat detection and swift incident response capabilities. Renowned for its advanced machine learning features, Cortex XDR seamlessly integrates with various Palo Alto Networks products, enhancing its overall effectiveness.
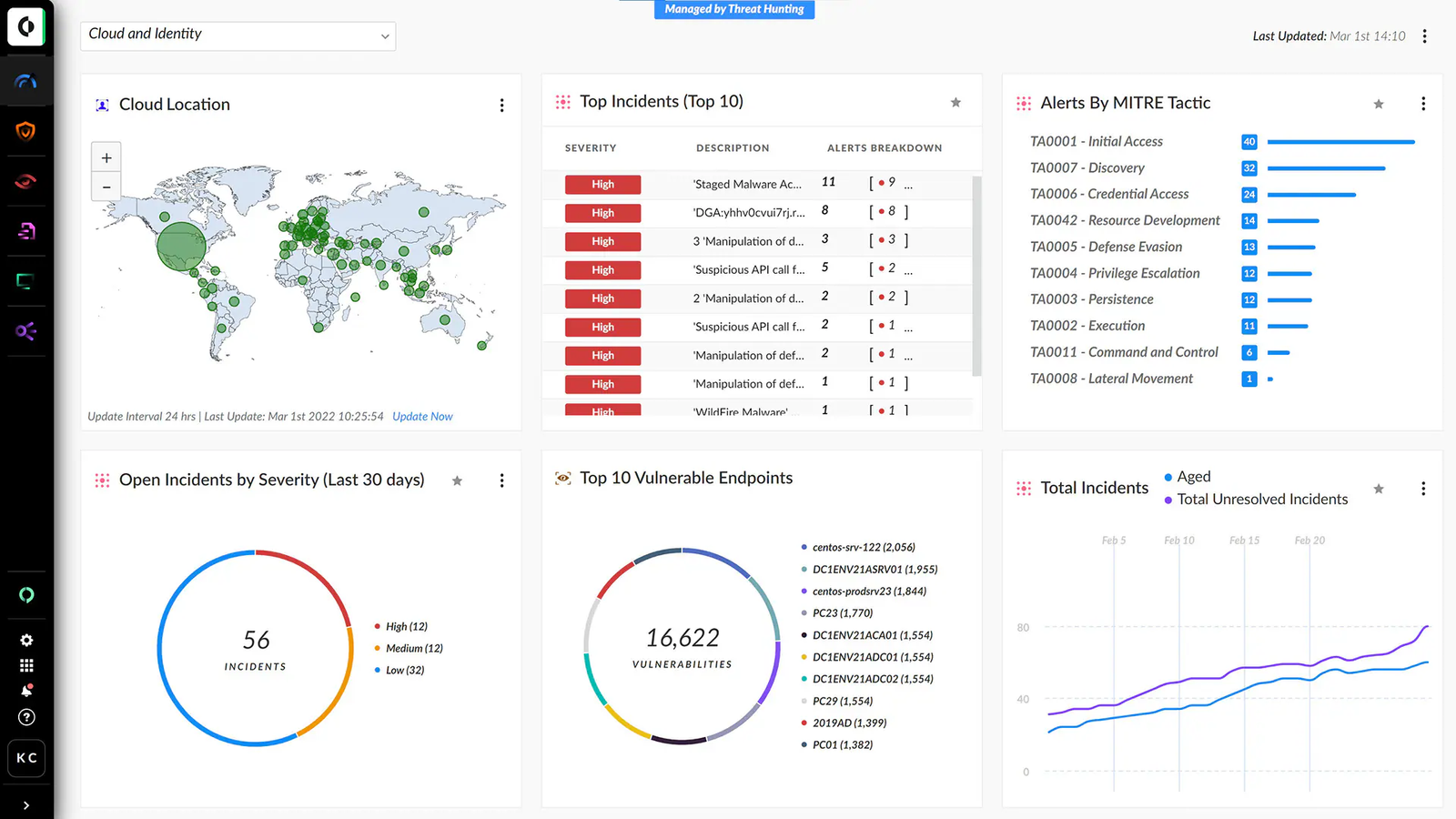
- SentinelOne Singularity: Singularity is a cloud-based EDR solution that is known for its ease of use and its ability to scale to large enterprises. It offers a variety of features, including endpoint detection, threat hunting, and automated remediation.
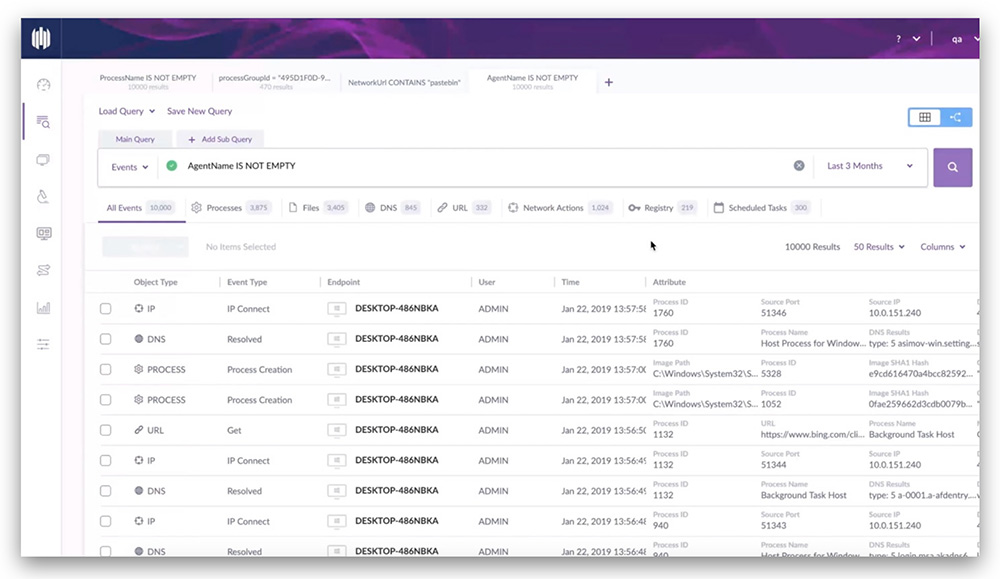
- CrowdStrike Falcon Insight XDR: Falcon Insight XDR is another cloud-based EDR solution that is known for its strong detection capabilities and its use of machine learning to identify threats. It offers a variety of features, including endpoint detection, threat hunting, and incident response.
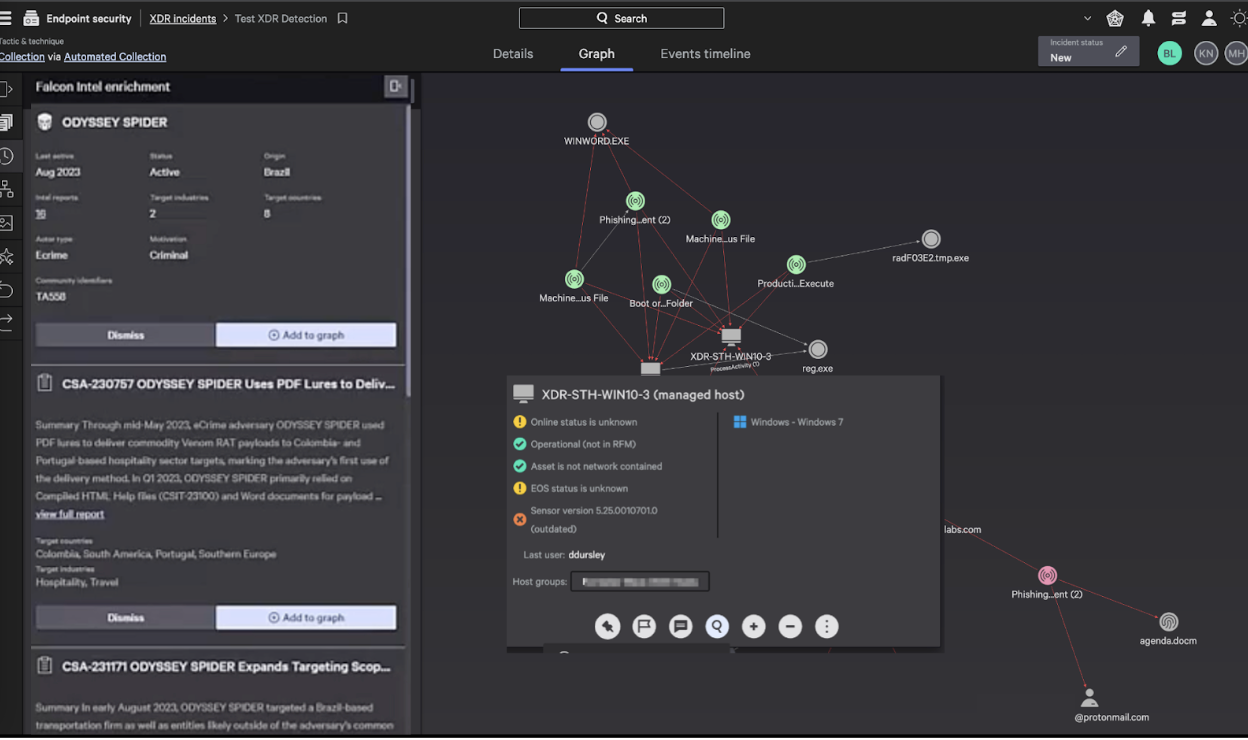
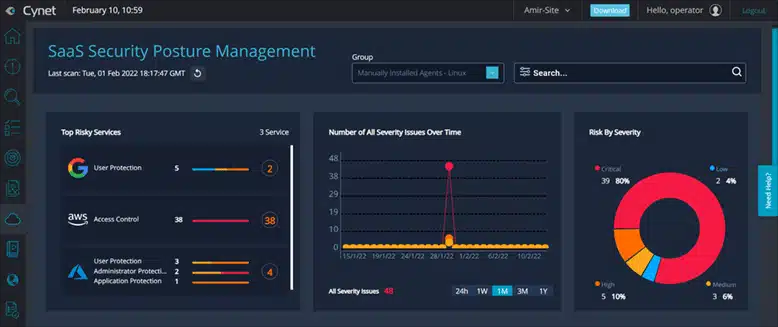
- Cynet 360 AutoXDR: AutoXDR is a cloud-based EDR solution that is known for its automated response capabilities and its ability to integrate with third-party security products. It offers a variety of features, including endpoint detection, threat hunting, and automated remediation.
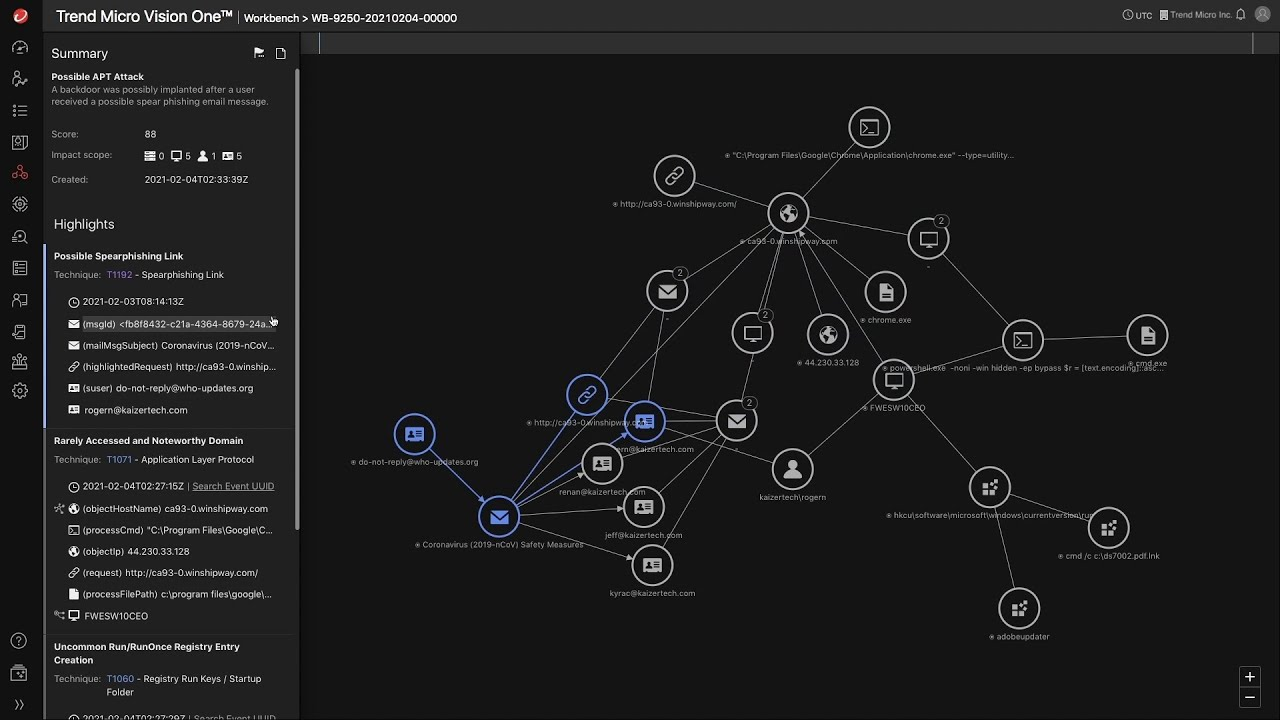
- Trend Micro XDR: XDR is a cloud-based EDR solution that is known for its ability to detect threats across multiple data sources, including endpoints, networks, and cloud environments. It offers a variety of features, including endpoint detection, threat hunting, and incident response.
These are just a few of the many EDR tools available on the market. The best tool for your organization will depend on your specific needs and requirements.
Conclusion
In the face of today’s rapidly changing threat environment, EDR stands as an essential tool for organizations aiming to shield their data and systems. The adoption of EDR grants organizations a pivotal advantage in their battle against cyber threats.
Additional Resources
Endpoint Detection and Response (EDR)
What is Endpoint Detection and Response (EDR)?
I hope this blog post has been informative. If you have any questions, please feel free to leave a comment below.
-VirusZzWarning



