
Local File Inclusion (LFI) Vulnerability: Safeguarding Systems
Imagine this: with just one click, your entire system could be exposed to alarming cyber threats. Welcome to the realm of Local File Inclusion (LFI), a hidden peril that demands urgent attention in the digital landscape.
In the realm of cybersecurity, comprehending vulnerabilities is paramount. LFI isn’t merely a buzzword; it serves as a potential gateway for malicious attackers to compromise your system’s integrity. However, fear not, for knowledge stands as your greatest shield in this ongoing battle for digital security.
What Exactly is Local File Inclusion (LFI)?
At its core, Local File Inclusion (LFI) represents a vulnerability that allows attackers to manipulate input parameters, consequently including files stored locally on a server. Predominantly found within web applications, LFI facilitates the unauthorized viewing of sensitive files, execution of malicious code, and potential access to restricted areas. Additionally, this vulnerability serves as a gateway for attackers to traverse directories, leveraging loopholes in code to navigate the server’s file structure. Such exploitation poses grave risks, thereby necessitating stringent preventive measures.
The Anatomy of LFI: How Does it Work?
This exploit sneaks in when web apps trustingly include files without a second thought. Attackers exploit input parameters, tricking apps into fetching arbitrary files. By toying with directory traversal sequences, they navigate through the file system, grabbing files they’re not meant to see.

Modes of LFI Assault
Understanding the diverse tactics attackers use is key to shoring up your defenses. LFI attacks come in two primary flavors:
1. File Inclusion Attack:
This mode involves manipulating input parameters in a way that enables attackers to insert external or local malicious files into vulnerable code. Attackers exploit weak input validation to include files that execute arbitrary code or grant access to sensitive data. For instance, an attacker might modify a URL parameter within a web application to include a file hosted externally, thereby executing malicious scripts or commands.
2. Directory Traversal:
Directory Traversal, also known as Path Traversal, involves manipulating file paths by using directory navigation characters such as ../ to traverse through directories. Attackers leverage this technique to move beyond the intended directory structure and access sensitive files or directories. For instance, an attacker could exploit a vulnerable parameter to navigate from a web application’s intended directory to system directories, potentially accessing critical files like configuration files, user databases, or system logs.

3. Poisoning via PHP Wrappers:
PHP Wrappers, such as php://, function as protocols enabling access to diverse input/output streams within PHP. Exploited by attackers, these wrappers manipulate file inclusion mechanisms, granting access to local files or command execution. For instance, leveraging php://input or php://filter, attackers can read input data or manipulate streams to execute arbitrary code seamlessly.

4. Windows LFI:
In Windows environments, attackers exploit LFI vulnerabilities inherent to Windows file systems. Employing traversal sequences such as ….\ within URLs, they attempt to traverse directories, aiming to access critical Windows-specific files like win.ini or other system configurations. These manipulations enable attackers to target sensitive system-related files on Windows servers by exploiting directory traversal techniques.
C:\Apache\conf\httpd.conf
C:\Apache\logs\access.log
C:\Apache\logs\error.log
C:\Apache2\conf\httpd.conf
C:\Apache2\logs\access.log
C:\Apache2\logs\error.log
C:\Apache22\conf\httpd.conf
C:\Apache22\logs\access.log
C:\Apache22\logs\error.log
C:\Apache24\conf\httpd.conf
C:\Apache24\logs\access.log
C:\Apache24\logs\error.log
C:\Documents and Settings\Administrator\NTUser.dat
C:\php\php.ini
C:\php4\php.ini
C:\php5\php.ini
C:\php7\php.ini
C:\Program Files (x86)\Apache Group\Apache\conf\httpd.conf
C:\Program Files (x86)\Apache Group\Apache\logs\access.log
C:\Program Files (x86)\Apache Group\Apache\logs\error.log
C:\Program Files (x86)\Apache Group\Apache2\conf\httpd.conf
C:\Program Files (x86)\Apache Group\Apache2\logs\access.log
C:\Program Files (x86)\Apache Group\Apache2\logs\error.log
c:\Program Files (x86)\php\php.ini
C:\Program Files\Apache Group\Apache\conf\httpd.conf
C:\Program Files\Apache Group\Apache\conf\logs\access.log
C:\Program Files\Apache Group\Apache\conf\logs\error.log
C:\Program Files\Apache Group\Apache2\conf\httpd.conf
C:\Program Files\Apache Group\Apache2\conf\logs\access.log
C:\Program Files\Apache Group\Apache2\conf\logs\error.log
C:\Program Files\FileZilla Server\FileZilla Server.xml
C:\Program Files\MySQL\my.cnf
C:\Program Files\MySQL\my.ini
C:\Program Files\MySQL\MySQL Server 5.0\my.cnf
C:\Program Files\MySQL\MySQL Server 5.0\my.ini
C:\Program Files\MySQL\MySQL Server 5.1\my.cnf
C:\Program Files\MySQL\MySQL Server 5.1\my.ini
C:\Program Files\MySQL\MySQL Server 5.5\my.cnf
C:\Program Files\MySQL\MySQL Server 5.5\my.ini
C:\Program Files\MySQL\MySQL Server 5.6\my.cnf
C:\Program Files\MySQL\MySQL Server 5.6\my.ini
C:\Program Files\MySQL\MySQL Server 5.7\my.cnf
C:\Program Files\MySQL\MySQL Server 5.7\my.ini
C:\Program Files\php\php.ini
C:\Users\Administrator\NTUser.dat
C:\Windows\debug\NetSetup.LOG
C:\Windows\Panther\Unattend\Unattended.xml
C:\Windows\Panther\Unattended.xml
C:\Windows\php.ini
C:\Windows\repair\SAM
C:\Windows\repair\system
C:\Windows\System32\config\AppEvent.evt
C:\Windows\System32\config\RegBack\SAM
C:\Windows\System32\config\RegBack\system
C:\Windows\System32\config\SAM
C:\Windows\System32\config\SecEvent.evt
C:\Windows\System32\config\SysEvent.evt
C:\Windows\System32\config\SYSTEM
C:\Windows\System32\drivers\etc\hosts
C:\Windows\System32\winevt\Logs\Application.evtx
C:\Windows\System32\winevt\Logs\Security.evtx
C:\Windows\System32\winevt\Logs\System.evtx
C:\Windows\win.ini
C:\xampp\apache\conf\extra\httpd-xampp.conf
C:\xampp\apache\conf\httpd.conf
C:\xampp\apache\logs\access.log
C:\xampp\apache\logs\error.log
C:\xampp\FileZillaFTP\FileZilla Server.xml
C:\xampp\MercuryMail\MERCURY.INI
C:\xampp\mysql\bin\my.ini
C:\xampp\php\php.ini
C:\xampp\security\webdav.htpasswd
C:\xampp\sendmail\sendmail.ini
C:\xampp\tomcat\conf\server.xml5. Command Injection via Local File Inclusion (LFI):
In specific scenarios, assailants exploit LFI vulnerabilities by injecting supplementary commands. This deceptive maneuver involves appending null bytes or other characters to the file path, adeptly bypassing security measures. Consequently, this technique allows for the execution of arbitrary commands on the server, potentially leading to system compromise or unauthorized access. Consequently, it poses a severe risk, potentially leading to system compromise or unauthorized access.
Practical Examples
Let’s cut through the theory with some real scenarios:
- Basic Local File Inclusion (LFI) Command:
http://vulnerablesite.com/page.php?file=filename.php- Directory Traversal:
http://vulnerablesite.com/page.php?file=../../../../etc/passwd- PHP Wrapper:
http://vulnerablesite.com/page.php?file=php://filter/convert.base64-encode/resource=config.php- Windows Local File Inclusion (LFI):
http://vulnerablesite.com/page.php?file=../../../../../Windows/win.ini- Command Injection via LFI:
http://vulnerablesite.com/page.php?file=../../../../var/log/apache/access.log%00How to Detect and Prevent Local File Inclusion (LFI) Attacks
Vigilance is the key to thwarting LFI attacks. Implementing robust security measures, such as input validation, output encoding, and restricting file access permissions, forms the first line of defense. Regularly updating and patching applications is imperative to mitigate known vulnerabilities.
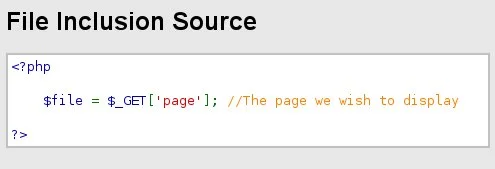
Exemplifying the Threat
Picture a vulnerable web app:

This vulnerability enables attackers to maneuver file paths, breaching security.
Securing Against Local File Inclusion (LFI)
Prevention’s the game. Consider this approach:
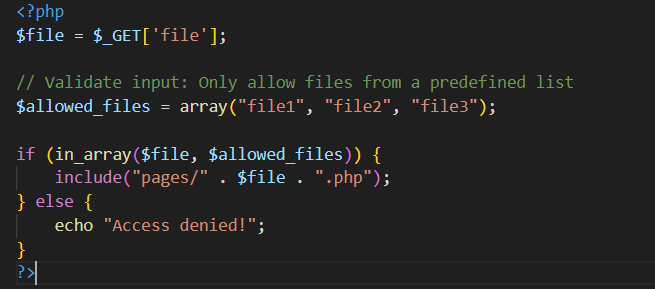
Validating inputs restricts file inclusion to an approved list, curtailing arbitrary access.
Fortifying Your System
1. Input Validation and Sanitization:
To bolster your defenses, prioritize implementing robust input validation measures. This involves thorough scrutiny and filtration of user-supplied inputs. Enforce stringent regulations regarding accepted input formats, file paths, and permissible characters. Ensure strict adherence to predefined patterns while promptly rejecting any deviations from these established standards. Additionally, sanitize inputs meticulously to eliminate or encode special characters that may be exploited for malicious traversal or injection purposes.
2. Whitelisting Allowed File Access:
Create a whitelist of allowed files or directories that the application can access. Rather than focusing on disallowing specific forbidden files, maintain a list of permitted files or paths. By restricting access to known, verified locations, you reduce the risk of unauthorized file inclusion.
3. Limit File Permissions:
Ensuring proper file permissions is pivotal in fortifying system security. By restricting unauthorized access to sensitive files and implementing stringent measures, files unnecessary for web app functionality should maintain limited read/write/execute permissions for the web server user. This strategy not only bolsters security but also mitigates risks associated with potential Local File Inclusion (LFI) vulnerabilities.
4. Use Frameworks and Security Libraries:
Utilize secure coding frameworks and libraries equipped with inherent defenses against common vulnerabilities like Local File Inclusion (LFI). These tools commonly feature functions or methods that securely handle file inclusion, consequently reducing the risk of potential vulnerabilities. By employing these resources, you significantly fortify your system’s resilience against cyber threats.
5. Disable Directory Listing:
Disabling directory listing on web servers is imperative to thwart attackers’ access to file structures. With directory listing enabled, attackers glean insights, empowering them to craft targeted and potentially damaging attacks.
6. Web Application Firewall (WAF):
Deploy a Web Application Firewall that can detect and block malicious requests, including attempts to exploit LFI vulnerabilities. WAFs offer an additional layer of defense by analyzing incoming traffic and blocking potentially harmful requests before they reach the application.
Conclusion
In the realm of cybersecurity, Local File Inclusion (LFI) stands as a critical vulnerability, offering an open door for attackers to breach systems. Understanding its modes of attack—from file inclusions to directory traversals—is key. Yet, fortifying against LFI demands more than technical measures; it requires a culture of vigilance, education, and continuous improvement. By implementing robust input validation, file whitelisting, and staying updated, we pave the way for a more secure digital landscape. Together, let’s fortify our systems and pave the path towards a safer digital future.



