
Zero-Day Exploits: The Hidden Threat to Cybersecurity
In the world of cybersecurity, zero-day exploits have become a buzzword, often associated with high-level attacks and sophisticated hacking campaigns.
But what exactly is it and how do they work?
This blog post will explore and discover the process of their discovery, and examine the
threats they pose to organizations and individuals.
Contents
- What is a Zero-Day Exploit?
- What discovers Zero-Day Exploits?
- How do Zero-Day Exploits Work?
- How are Zero-Day Exploits Used by Attackers?
- Protecting Yourself from Zero-Day Exploits
- The Stuxnet Attack
- WannaCry
- Operation Aurora
- Conclusion
What is a Zero-Day Exploit?
A zero-day exploit is a type of vulnerability in software that the vendor is unaware of and has yet to fix.
The term “zero-day” reflects the fact that the vendor has had zero days to address the vulnerability since its discovery. In other words, it is a measure of the time elapsed since the vulnerability was first uncovered.
Once discovered, attackers can exploit the vulnerability to launch malicious attacks
on organizations and individuals, often leading to data theft, unauthorized access, and other serious security incidents.

What discovers Zero-Day Exploits?
Security researchers or hackers often discover these exploits as they search for vulnerabilities in software and operating systems.
In some cases, the discovery of these type of exploit is accidental, while in other cases it is
the result of a deliberate search for vulnerabilities.
Once discovered, black market traders sell or trade these exploits, offering attackers the opportunity to launch attacks.
How do Zero-Day Exploits Work?
Zero-day exploits work by taking advantage of a vulnerability in software or an operating system.
For example, a “0-day”exploit might take advantage of a flaw in the code that allows
an attacker to bypass security measures and gain access to sensitive information.
The exploit could also allow the attacker to execute arbitrary code, install malware, or take control of the system.
How are Zero-Day Exploits Used by Attackers?
Attackers can utilize a newly discovered zero-day exploit in various ways.
For example, attackers might use the exploit to launch targeted attacks against specific
organizations or individuals, such as government agencies, financial institutions, or high-level executives.
In these cases, the attacker’s goal is often to steal sensitive information, disrupt operations, or cause damage to the organization.
Large-scale attacks, such as ransomware attacks or data breaches, can also utilize zero-day exploits.
In these cases, the attacker might use the exploit to gain access to large numbers of systems,
encrypting data or stealing sensitive information from a large number of victims.

Protecting Yourself from Zero-Day Exploits
The best way to protect yourself from these types of exploits is to keep your software and operating systems up-to-date.
Reducing the risk of an attack requires promptly patching vulnerabilities as soon as they are discovered.
Additionally, using strong passwords, enabling two-factor authentication, and using anti-virus software
can also help protect against exploits and other security threats.
The Stuxnet Attack
The Stuxnet attack was a highly sophisticated cyberattack that targeted the Iranian nuclear program in 2010.
The attack used a zero-day exploit in the Windows operating system to spread the malware
from computer to computer, eventually reaching the systems that controlled the centrifuges used in Iran’s nuclear program.
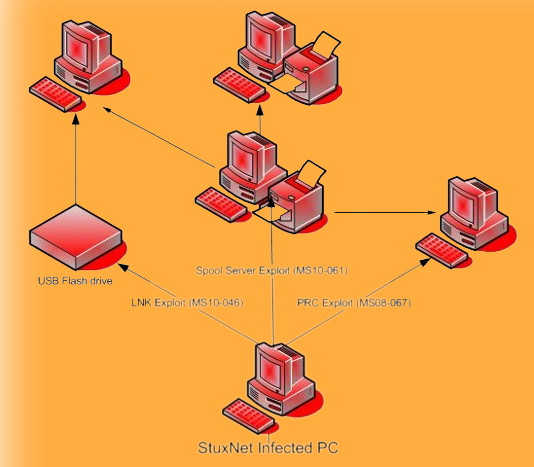
The malware caused the centrifuges to spin out of control, effectively destroying them and setting back the Iranian nuclear program by several years.
The Stuxnet attack was a prime illustration of the perils posed by zero-day exploits. By taking advantage of a previously undiscovered vulnerability, the attackers were able to launch a highly targeted and successful attack, demonstrating the potential dangers of these exploits.
Furthermore, it highlights the importance of regularly updating software and systems to reduce the risk of exploitation.
The incident also highlights the importance of keeping software and operating systems up-to-date, as well as the need for strong security measures to protect against the threats posed by zero-day exploits.
The impact of Stuxnet
The impact of the Stuxnet attack is difficult to quantify, but it is widely considered
to be one of the most significant cyber attacks in history.
The attack set back the Iranian nuclear program by several years, and it raised awareness of the potential dangers posed by zero-day exploits and state-sponsored cyber attacks.
The response to Stuxnet
The Stuxnet attack prompted a significant response from the international community, including
both private-sector organizations and governments.
Many organizations took steps to improve their cybersecurity in the wake of the attack, and governments
around the world began to take a more active role in protecting their critical infrastructure from similar threats.
WannaCry

The Shadow Brokers hacking group leaked a zero-day exploit in Microsoft Windows, known as EternalBlue, that the U.S. National Security Agency had developed. The WannaCry attackers then utilized this exploit, resulting in the rapid spread of a ransomware attack across the world in May 2017 and the infection of hundreds of thousands of systems in over 150 countries.
The impact of WannaCry
The WannaCry attack had a significant impact on individuals and organizations around the world.
Temporary shutdown of operations and significant financial losses were suffered by many businesses as a result of the attack.
The attack also affected healthcare organizations, causing disruption to medical facilities and putting patients at risk.
Many individuals had their personal information
and files held for ransom, causing significant stress and financial hardship.
The response to WannaCry
In response to the WannaCry attack, Microsoft released a patch for the EternalBlue vulnerability, and many organizations took steps to protect their systems and networks against similar attacks in the future.
Moreover law enforcement agencies around the world launched investigations into the attack,
and some individuals were arrested and charged in connection with the attack.
The WannaCry attack was a wake-up call for many organizations, highlighting the importance of staying vigilant against zero-day threats and taking proactive steps to protect against such attacks.
Operation Aurora
In 2009 and 2010, a highly sophisticated cyber attack named Operation Aurora targeted a number of high-tech companies, including Google, using a zero-day exploit in Internet Explorer to gain access to their systems and steal sensitive information.

The attack, widely believed to have originated from China and state-sponsored, caused widespread concern in the tech community.
The impact of Operation Aurora
These attack had a significant impact on the targeted organizations, particularly in the high-tech sector.
Mny companies suffered financial losses as a result of the theft of sensitive information and intellectual property.
The attack raised concerns about the vulnerability of sensitive information and the potential for state-sponsored cyber attacks to cause significant harm.
The response to Operation Aurora
After being targeted by the Operation Aurora attack, the affected organizations took action to enhance their cybersecurity measures and prevent future breaches.
They fortified their systems and invested in improving their security infrastructure, including by using firewalls, intrusion detection systems, and anti-virus software. These efforts aimed to safeguard against similar attacks in the future.
Conclusion
In conclusion, the operation and usage of these types of exploits by attackers pose a significant threat
to both organizations and individuals, making it crucial to comprehend how they work.
To comprehend their potential impact, one must have a thorough understanding of how they work.
By keeping your software and operating systems up-to-date and taking other security measures,
you can reduce the risk of an attack and protect your data and systems from harm.
– VirusZzWarning
Tag:security, stuxnet, zero day, zero day attack



