
NMAP – To Find Network Vulnerabilities
In this blog, I’ll discuss NMAP, which is a free and essential tool for hackers and pretty much anyone in IT. NMAP is a network scanner created by Gordon Lyon. NMAP is used to discover hosts and services on a computer network by transferring packets and
analysing the responses. We can scan the entire network, find our targets,
Find out what operating system our target is using and which ports are open.
And even we can find vulnerabilities that can be exploited. This is the power of NMAP.
Let’s get started!!
NMAP
NMAP, or Network Mapper, is the tool used by hackers to scan networks so we can
Find live hosts or targets to hack. And we can also use NMAP to find more
information about these targets.
NMAP is compatible with all operating systems, including Windows, Mac, and Linux.
In my case, I’ll be using Kali Linux.
Pinging all the available hosts in our network
So, generally, to ping a device on any network, we just type the following command
and check whether the device is running or not.
ping <ip address>
But what if I want to scan the whole network and check which devices are running on our network?
Let’s assume our home network is 192.106.54.2/24, which means there could be 254 endpoints
or hosts available on our network. So it is not possible for a normal human
to use the ping command and check whether any hosts are running on the network.
For these, there is a simple NMAP command to scan the whole network and show which host is up.
nmap -sP <ip address>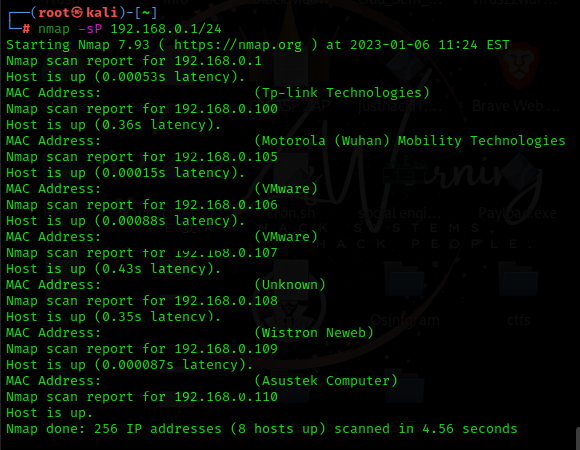
As a hacker, knowing that the hosts are operational is insufficient; we require more information.
If we look at the scanning methodology that the EC-Council goes by, we just covered the first step,
which is “checking for live systems.”
Now we need to find open ports, which is the second step.

Checking for Open Ports.
Assume I want to hack a website and find all network endpoints that are running a website.
What am I going to look for?
We typically look at ports like 80 or 443. These ports will typically be open on a server if it’s running a website.
For checking whether ports 80 and 443 are open, the command goes like this:
nmap -sT -p 80,443 <ip address>
Here -sT is a type of port scan called the TCP connect, or you might see it as a “full open scan.”
which performs a 3-way handshake and provides us with these results.
NMAP STEALTH mode.
What is the purpose of stealth mode?
We need stealth mode because, in some cases, NMAP commands might act intrusive, and security measures like a firewall or IDS can block the request from proceeding further. So for that, we will use the following command:
nmap -sS -p <ports> <ip address>
Stealth scanning is also known as SYN scanning or half-open scanning. This scan is used to avoid 3-way handshakes and firewalls and try to complete the scan. But in today’s time, you can also get caught by firewalls by using the stealth scanning method.
NMAP Manual.
Nmap can do a lot more things; write the following command and it will provide you with all types of switches you can use for scanning.
man nmapTo know what operating system your target is using, just type the following command:
nmap -O <ipaddress>
It will give you details about your target’s system and also tell you which ports are open.
NMAP Scripts.
All the above commands that I discussed are informative, but NMAP also has its scripting engine, which will let you write scripts and break into your target machine.

Now that these are all the categories under the NMAP Scripting Engine, let’s say a category called “vuln,” which is vulnerability. When we scan a system with this category, it will tell you which ports are open and if the machine is up, but it will also tell you the vulnerabilities that the system has, and this is the crazy part. If anyone comes to know about a vulnerability in any system, they can simply exploit the vulnerability and take control of the system.
nmap --script <script> <ip address>There are several scripts listed under the “vuln” category, but it is not possible for an attacker to check each script.
So for that, an attacker can just type, nmap --script vuln 10.13.1.82.
It will try every item on the list until it finds the actual vulnerability in the system. This example was for
scripts in the “vuln” category You can do this with any category, you just need to follow the following command:
nmap --script <script category> <ip address>This was just a quick overview of NMAP. There are several switches and scanning options in NMAP; if you want to try them and master them, you need to practise them all. You can use the official NMAP manual to check all the switches and scanning options. And if you want to become a hacker or opt for CEH certifications, you will have to master all the NMAP commands. There are more scanning options, like controlling the speed of scanning; the default is -T3. You need to learn all these things to master hacking.
Nmap: your first line of defense in cyber security!!
With ♥ VirusZzWarning



